Quiz Summary
0 of 8 Questions completed
Questions:
Information
You have already completed the quiz before. Hence you can not start it again.
Quiz is loading…
You must sign in or sign up to start the quiz.
You must first complete the following:
Results
Results
0 of 8 Questions answered correctly
Your time:
Time has elapsed
You have reached 0 of 0 point(s), (0)
Earned Point(s): 0 of 0, (0)
0 Essay(s) Pending (Possible Point(s): 0)
Categories
- Not categorized 0%
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- Current
- Review / Skip
- Answered
- Correct
- Incorrect
-
Question 1 of 8
1. Question
Who should be responsible for the risk management process in an organization?
CorrectIncorrect -
Question 2 of 8
2. Question
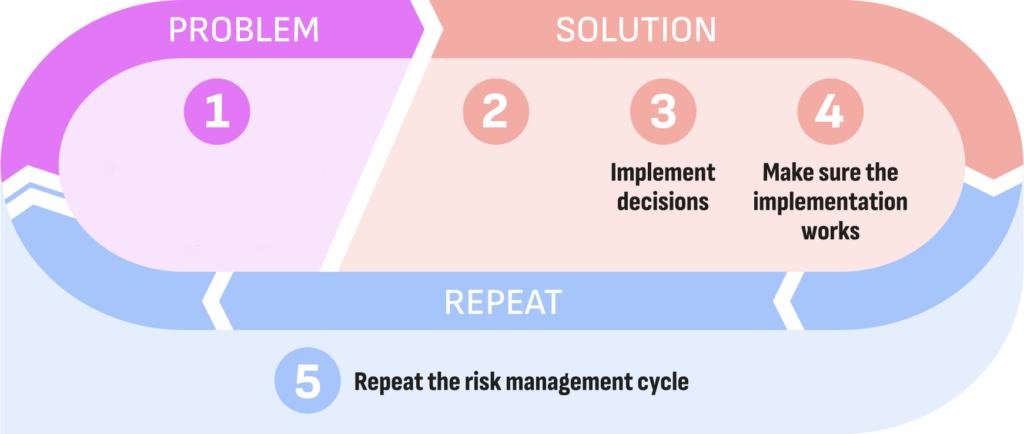
Reorganize the steps of the risk management process in the correct order to find out which come first:
CorrectIncorrect -
Question 3 of 8
3. Question
Match the following statements by dragging and dropping them into the correct pairs:
Sort elements
- Helps us specify what we want to protect
- Is a list of assets
- Has to be regularly updated
- Include everything we want to protect
-
Assets enumeration
-
The output of the assets enumeration
-
The list of assets
-
Assets
CorrectIncorrect -
Question 4 of 8
4. Question
Which of the following statements describes the threat modeling process?
CorrectIncorrect -
Question 5 of 8
5. Question
Four months ago, your organization was hit by a DDoS attack, temporarily shutting down your website and disrupting communications. As you assess your future cybersecurity risks, how should you rate the probability of facing another DDoS attack?
CorrectIncorrect -
Question 6 of 8
6. Question
Your organization’s financial director’s email has been hacked! But before panicking, you need to assess the potential impact. How serious could this breach be?
CorrectIncorrect -
Question 7 of 8
7. Question
How would you define a “risk”?
Please enter your own definition based on the materials provided in this e-course so far:
-
This response will be awarded full points automatically, but it can be reviewed and adjusted after submission.
Grading can be reviewed and adjusted.Grading can be reviewed and adjusted. -
-
Question 8 of 8
8. Question
How can a risk be dealt with? Match the correct pairs by dragging and dropping them:
Sort elements
- Eliminate the risk by completely not doing the activity that might cause the risk
- Develop and implement security measures that scale down the impact and likelihood of the risk
- Partially or fully share the risk with someone else
- Acknowledge the risk and do nothing about it
CorrectIncorrect