Human rights defenders play a crucial yet demanding role in protecting human rights, often facing significant challenges. Their work is hindered by shrinking civic space, hostile environments, and adversaries who use physical, digital, or legal threats. These risks, including mental health challenges like burnout and distress, are interconnected and can drain valuable resources. Investing in security is essential and should involve allocating the right resources to help prevent these threats. This is where a risk management process can make a difference. This e-course aims to equip human rights defenders with essential knowledge and skills to manage different risks and to tailor the measures specifically to their contexts. Let’s dive into it together!
What will you learn?
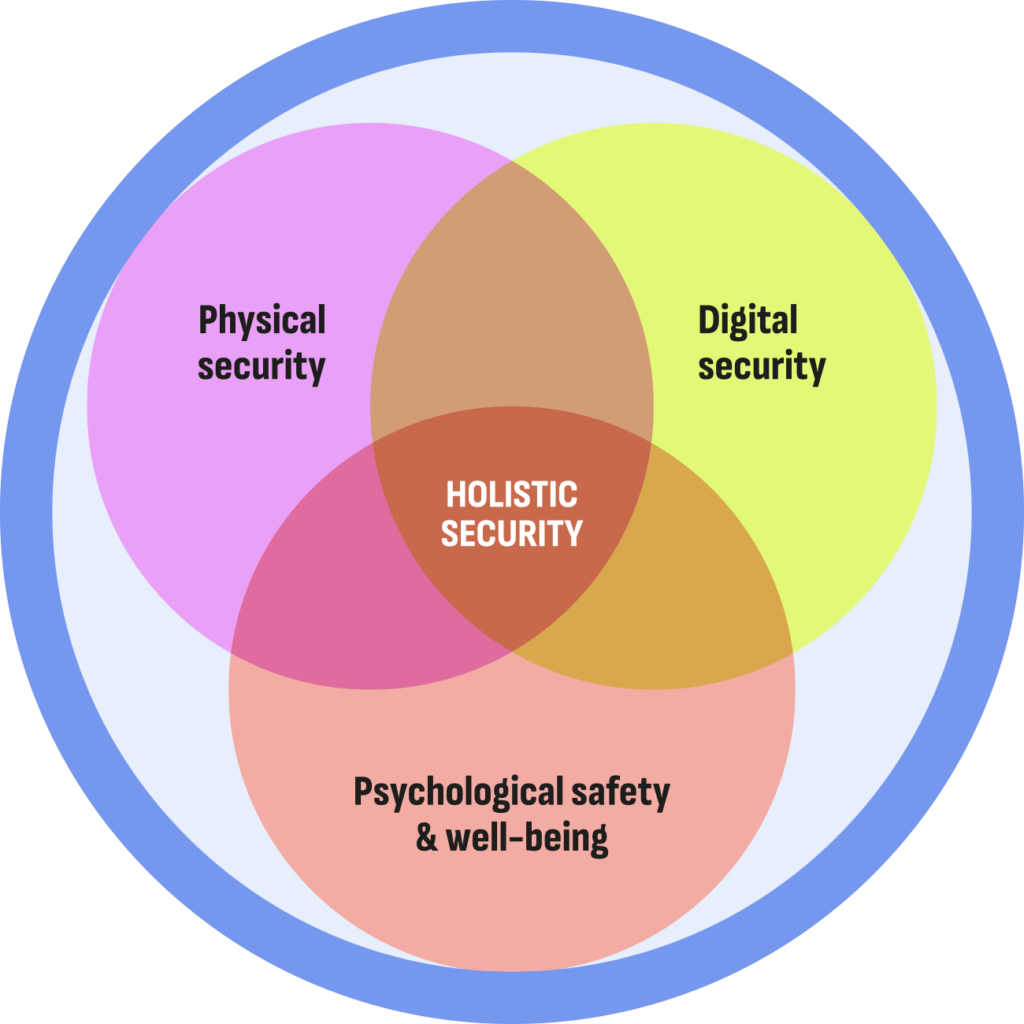
Risk management requires a holistic approach to security. You will learn how the physical, digital, and psychological implications of safety and security are interconnected, influence each other, and why they require your attention all together and not in isolation from each other.
Risk management is a systematic and cyclic process. You will learn how to identify and prioritize key risks, determine effective mitigation strategy, implement these measures, verify their effectiveness, and continuously adapt the measures based on evolving threats and your context.
There is no one-size-fits-all approach to security. You will learn that a robust approach to security requires a sound understanding and assessment of your context, of the individual characteristics and background of all people involved, as well as your existing capacities and vulnerabilities.
Managing risks is not a one-person job. You will discover the importance of collaborating with team members, consulting experts, and leveraging diverse perspectives to make informed decisions and better address security risks.
Meet the team behind the course
Trainers and contributors collaborated with ODIHR to develop this training course, applying their professional expertise to shape the content. This ensures you to gain essential knowledge for conducting effective risk management processes.
Trainers
 | Mykola Kostynyan is a digital security expert designing and implementing national and regional programs and projects across Eastern Europe, focusing on systematic assistance and support to civil society and independent media organizations. He also develops and leads regional capacity and network building programs for digital security service providers working with these sectors. |
 | Sasha Delemenchuk is the founder of the Tbilisi Shelter City project, dedicated to protecting human rights defenders. She is a certified security trainer with Front Line Defenders and a trainer for the International Hague Course on Human Rights. As a co-founder of the EuromaidanSOS volunteer initiative, she has been actively involved in human rights advocacy and crisis response. Sasha has extensive experience working in Ukraine, Georgia, Armenia, Azerbaijan, Belarus, Moldova, Kazakhstan, South Sudan, Kenya, Tajikistan, and Nepal. |
 | Angelica Notaristefano is a former Assistant Project Officer at the OSCE Office for Democratic Institutions and Human Rights (ODIHR) with extensive experience in human rights monitoring. Her work has been focusing on monitoring the situation of human rights defenders in the OSCE region and beyond, as well as developing capacity building activities for human rights defenders on topics related to human rights monitoring, safety and security and the right to freedom of peaceful assembly. |
 | Marine Constant is a Human Rights Advisor / Capacity Building Coordinator at the OSCE Office for Democratic Institutions and Human Rights (ODIHR), where she oversees capacity building initiatives for human rights defenders, through the use of innovative technology solutions. She has more than 10 years’ experience in the field of human rights monitoring, advocacy, and capacity building, and worked across the OSCE region and South East Asia. |
Contributors
- Kakhaber Mikadze, Psychotherapist, Trainer, Tbilisi Shelter City
- Lasha Dzigrashvili, Doctor of Medicine, Executive Director of Tbilisi Shelter City
- Agit Mirzoev, Security Trainer, Head of Educational Programs of Tbilisi Shelter City
- Zala Čas, Assistant Project Officer at OSCE Office for Democratic Institutions and Human Rights (ODIHR)
Learn more about the OSCE Office for Democratic Institutions and Human Rights (ODIHR).
Modalities
How do I enroll?
The course is available for free and for all.
You may access it anytime with or without registration. However, registering enables you to:
1- Save your progress: stop at any stage and resume whenever you feel like it.
2- Obtain certificate upon successful completion: the name on your certificate will appear as the first name and second name noted at registration.
If you are having trouble exiting out of the log-in/registration panel, kindly zoom out to access the exit button.
Language and Subtitles
This course is available in two languages: English and Russian. Pick your language option at the top right bottom of this page. All videos are subtitled. To turn the subtitles on, click on the settings in the lower-right corner of a video and choose a language.
How do I get a certificate?
The module quizzes are compulsory but will not affect your final grade. These quizzes can be retaken and we encourage you to go back and refer to these materials as and when you need them.
At the end of the course – subject to completing all of the module quizzes – there is a final assessment that, if passed, will provide you with a certificate for completing the course.
Certificate Requirements
Complete the final assessment with a final grade of 75% or higher.
The content of this course has been separated into three modules, each containing three video lectures. Each video will guide you through the risk management cycle and provide you with useful examples and tips on how to follow the cycle and manage risks.
All modules contain mandatory and recommended additional resources, allowing you to explore some topics in more detail. You will be able to reflect on your knowledge by completing quizzes after each module and in a final assessment at the end of the course.
Note that this course does not aim to provide ready-to-implement solutions but rather offers an opportunity to reflect individually on how to apply the risk management process to your own context.